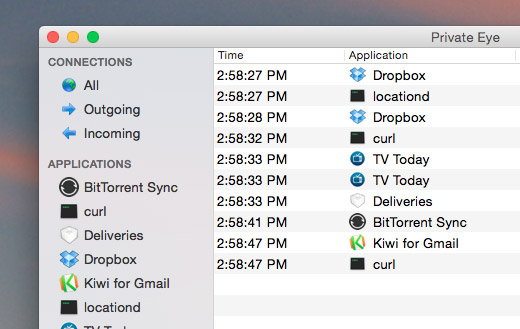
OS X v10.5.1 and later include an application firewall you can use to control connections on a per-application basis (rather than a per-port basis). This makes it easier to gain the benefits of firewall protection, and helps prevent undesirable apps from taking control of network ports open for legitimate apps.
Configuring the application firewall in OS X v10.6 and later
- Download essential protection with award-winning antivirus. Fast, powerful anti-malware protection for your Mac, whether you're browsing, working or gaming online.
- 'Gives you all the protection of the company's free firewall, plus advanced features, premium support, and innovative phishing protection' Excellent. PCMag Editor's Choice. The world's best firewall, tailored to your needs. Try free for 30 days. System requirements.
Use these steps to enable the application firewall:
Firewall For Mac Free Software
- Choose System Preferences from the Apple menu.
- Click Security or Security & Privacy.
- Click the Firewall tab.
- Unlock the pane by clicking the lock in the lower-left corner and enter the administrator username and password.
- Click 'Turn On Firewall' or 'Start' to enable the firewall.
- Click Advanced to customize the firewall configuration.
Configuring the Application Firewall in Mac OS X v10.5

Make sure you have updated to Mac OS X v10.5.1 or later. Then, use these steps to enable the application firewall:
- Choose System Preferences from the Apple menu.
- Click Security.
- Click the Firewall tab.
- Choose what mode you would like the firewall to use.
Advanced settings
Block all incoming connections
Selecting the option to 'Block all incoming connections' prevents all sharing services, such as File Sharing and Screen Sharing from receiving incoming connections. The system services that are still allowed to receive incoming connections are:
- configd, which implements DHCP and other network configuration services
- mDNSResponder, which implements Bonjour
- racoon, which implements IPSec
The firewall references a list of over two million known PC-friendly applications. If a file that is not on this safe-list knocks on your PC's door, the Firewall immediately alerts you to the possibility of attacking malware. All this occurs before the malware infects your computer. It's prevention-based security, the only way to keep PCs. TeamViewer Host is used for 24/7 access to remote computers, which makes it an ideal solution for uses such as remote monitoring, server maintenance, or connecting to a PC or Mac in the office or at home. Install TeamViewer Host on an unlimited number of computers and devices. As a licensed user, you have access to them all!
To use sharing services, make sure 'Block all incoming connections' is deselected.
Allowing specific applications
To allow a specific app to receive incoming connections, add it using Firewall Options:
- Open System Preferences.
- Click the Security or Security & Privacy icon.
- Select the Firewall tab.
- Click the lock icon in the preference pane, then enter an administrator name and password.
- Click the Firewall Options button
- Click the Add Application (+) button.
- Select the app you want to allow incoming connection privileges for.
- Click Add.
- Click OK.
You can also remove any apps listed here that you no longer want to allow by clicking the Remove App (-) button.
Automatically allow signed software to receive incoming connections
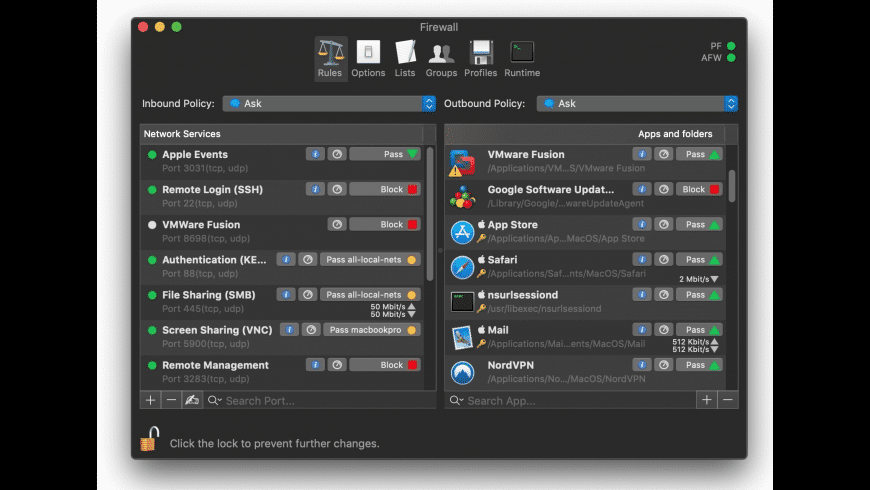
Applications that are signed by a valid certificate authority are automatically added to the list of allowed apps, rather than prompting the user to authorize them. Apps included in OS X are signed by Apple and are allowed to receive incoming connections when this setting is enabled. For example, since iTunes is already signed by Apple, it is automatically allowed to receive incoming connections through the firewall.
If you run an unsigned app that is not listed in the firewall list, a dialog appears with options to Allow or Deny connections for the app. If you choose Allow, OS X signs the application and automatically adds it to the firewall list. If you choose Deny, OS X adds it to the list but denies incoming connections intended for this app.
If you want to deny a digitally signed application, you should first add it to the list and then explicitly deny it.
Some apps check their own integrity when they are opened without using code signing. If the firewall recognizes such an app it doesn't sign it. Instead, it the 'Allow or Deny' dialog appears every time the app is opened. This can be avoided by upgrading to a version of the app that is signed by its developer.
Enable stealth mode
Enabling stealth mode prevents the computer from responding to probing requests. The computer still answers incoming requests for authorized apps. Unexpected requests, such as ICMP (ping) are ignored.
Firewall limitations
Firewall Software For Mac Free Download
The application firewall is designed to work with Internet protocols most commonly used by applications – TCP and UDP. Firewall settings do not affect AppleTalk connections. The firewall may be set to block incoming ICMP 'pings' by enabling Stealth Mode in Advanced Settings. Earlier ipfw technology is still accessible from the command line (in Terminal) and the application firewall does not overrule any rules set using ipfw. If ipfw blocks an incoming packet, the application firewall does not process it.
Powerful first line of defense
ZoneAlarm Pro Firewall gives you full control over your firewall, enabling you to configure it to your security needs by classifying your network settings. It targets and defeats new and advanced attacks that other firewalls miss, giving you maximum security against zero-day attacks.
Advanced Firewall
Firewall Free Download For Mac
Monitors programs for behaviors within your computer to spot and stop even the most sophisticated new attacks that bypass traditional firewall. Proactively protects against inbound and outbound attacks while making you invisible to hackers.
Identity Protection
Provides superior PC-based protection and exclusive data encryption, including offline identity-protection services. Moreover, Identity Protection monitors your credit report daily to see if any changes occur, keeping you alert of fraud, and provides you with recovery services if your identity had been stolen.
Anti-Phishing
ZoneAlarm Anti-Phishing protects your private information from a phishing attack while browsing online, securing your personal information from hackers and malicious websites. It scans all websites before letting you insert any personal information and alerts you whether it is a safe website or a phishing attempt.
